Configuración¶
La configuración de un masternode requiere una comprensión básica de Linux y la tecnología de la cadena de bloques, así como la capacidad de seguir las instrucciones de cerca. También requiere un mantenimiento regular y una seguridad cuidadosa, especialmente si no estás almacenando tus Dash en una billetera de hardware. Hay algunas decisiones que se tomarán en el camino, y pasos adicionales opcionales que tomar para una mayor seguridad.
Commercial masternode hosting services are available if you prefer to delegate day-to-day operation of your masternode to a professional operator. When using these hosting services, you retain full control of the 1000 DASH collateral and pay an agreed percentage of your reward to the operator. It is also possible to delegate your voting keys to a representative, see the governance documentation for more information.
Antes de comenzar¶
This guide assumes you are setting up a single masternode for the first time. If you are updating a masternode, see here instead. If Spork 15 is not yet enabled, it is not possible to directly set up a DIP003 masternode. You will need to set up the masternode following the old process and then work through the upgrade procedure. You will need:
- 1000 Dash
- Una billetera para guardar tus Dash, preferiblemente una billetera de hardware, aunque la billetera Dash Core también es compatible
- Un servidor Linux, preferiblemente un Servidor Privado Virtual (VPS)
Dash 0.13.0 implements DIP003, which introduces several changes to how a Dash masternode is set up and operated. A list of available documentation appears below:
- DIP003 Deterministic Masternode Lists
- DIP003 Masternode Changes
- Dash 0.13 Upgrade Procedure
- Full masternode setup guide (you are here)
- Information for users of hosted masternodes
- Information for operators of hosted masternodes
It is highly recommended to first read at least the list of changes
before continuing in order to familiarize yourself with the new concepts
in DIP003. This documentation describes the commands as if they were
entered in the Dash Core GUI by opening the console from Tools > Debug
console, but the same result can be achieved on a masternode by
entering the same commands and adding the prefix
~/.dashcore/dash-cli to each command.
Configurar tu VPS¶
A VPS, more commonly known as a cloud server, is fully functional installation of an operating system (usually Linux) operating within a virtual machine. The virtual machine allows the VPS provider to run multiple systems on one physical server, making it more efficient and much cheaper than having a single operating system running on the «bare metal» of each server. A VPS is ideal for hosting a Dash masternode because they typically offer guaranteed uptime, redundancy in the case of hardware failure and a static IP address that is required to ensure you remain in the masternode payment queue. While running a masternode from home on a desktop computer is technically possible, it will most likely not work reliably because most ISPs allocate dynamic IP addresses to home users.
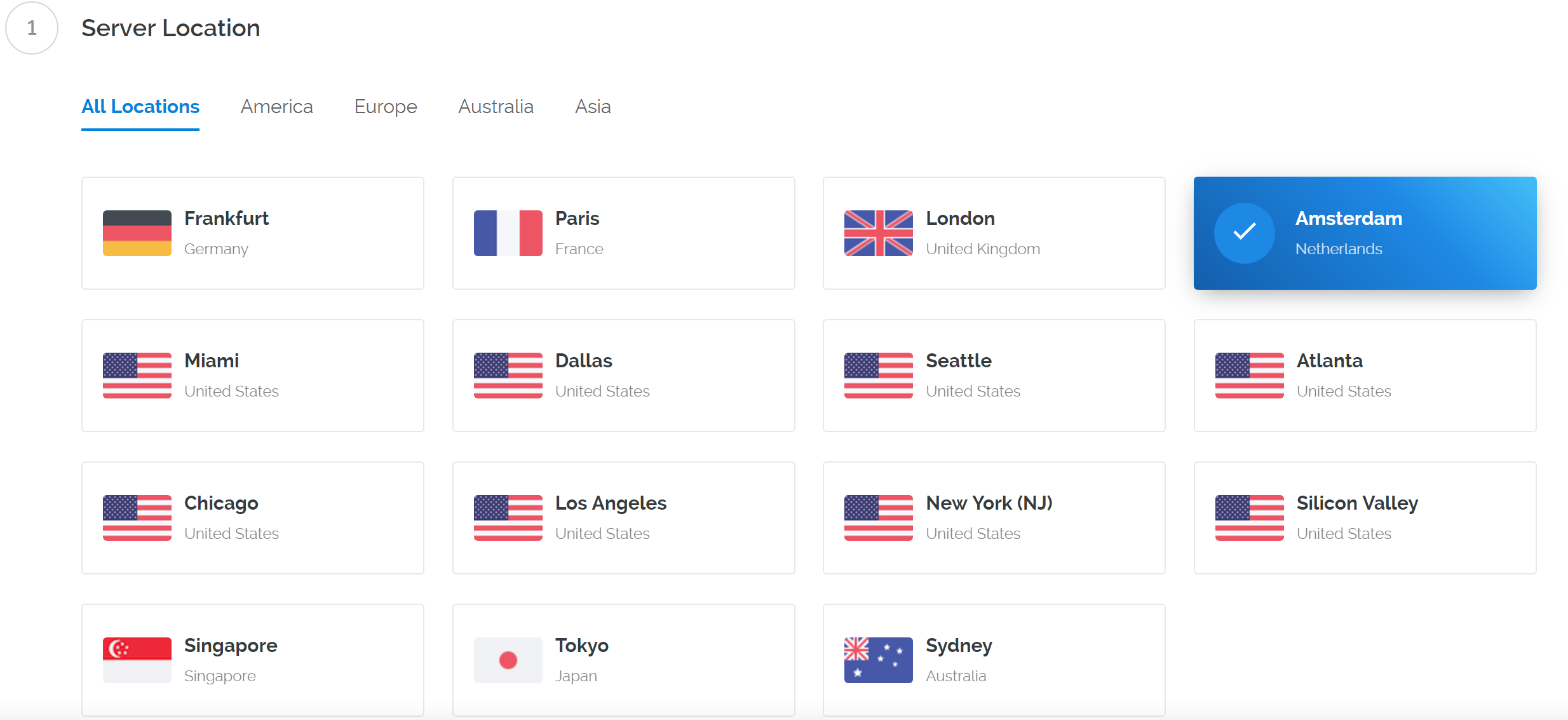
We will use Vultr hosting as an example of a VPS, although DigitalOcean, Amazon EC2, Google Cloud, Choopa and OVH are also popular choices. First create an account and add credit. Then go to the Servers menu item on the left and click + to add a new server. Select a location for your new server on the following screen:
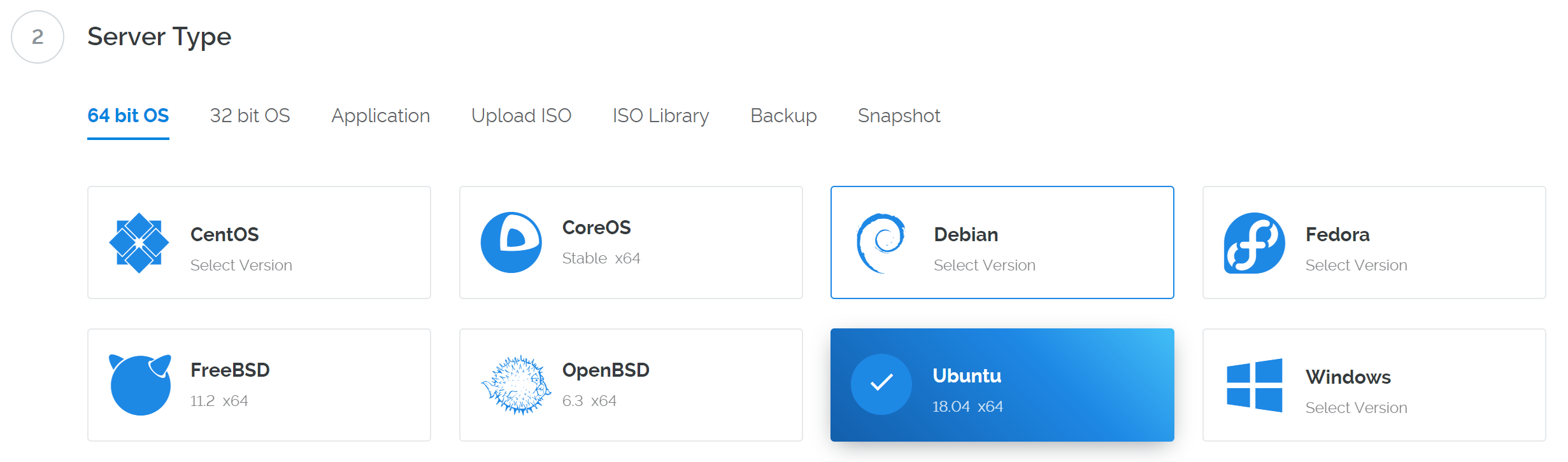
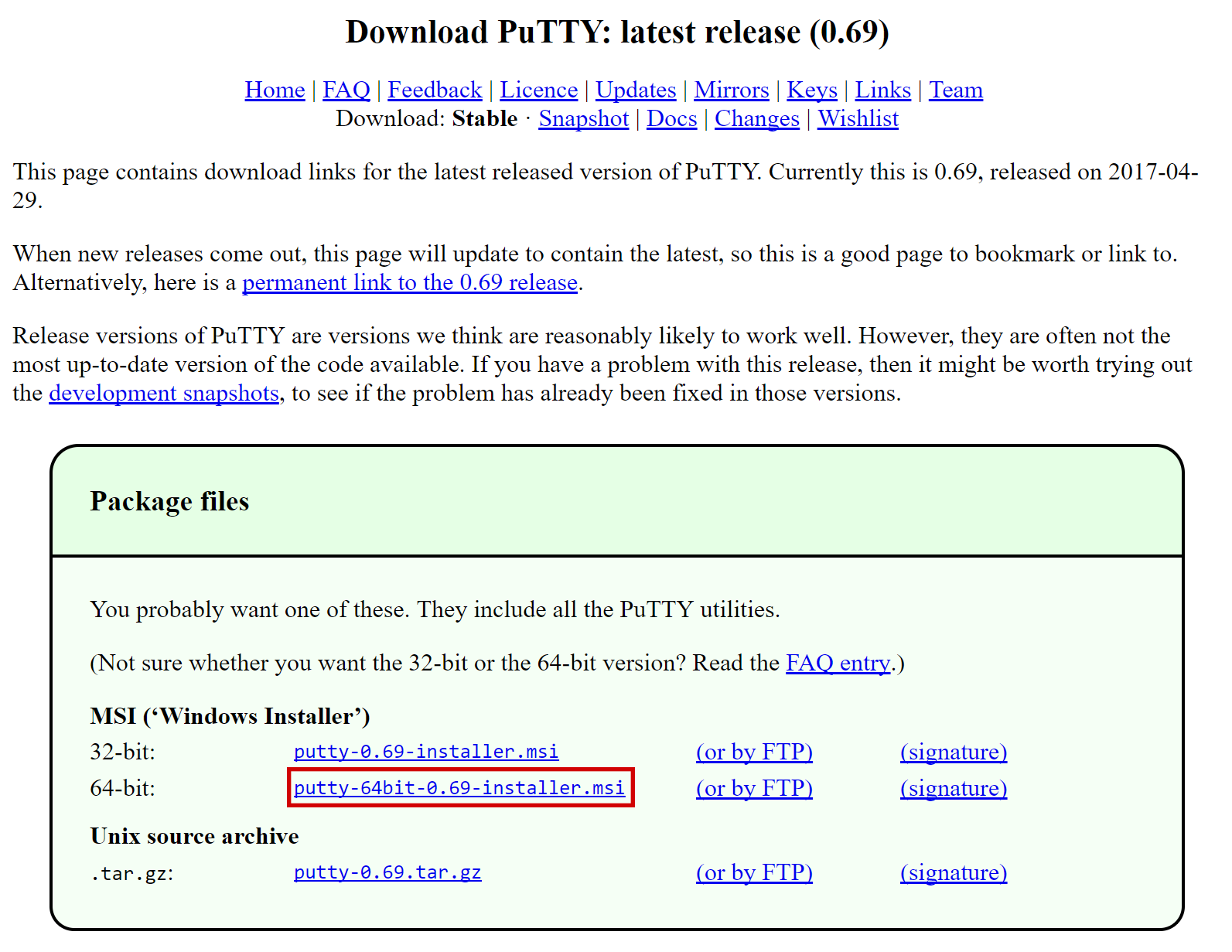
Select Ubuntu 18.04 x64 as the server type. We use this LTS release of Ubuntu instead of the latest version because LTS releases are supported with security updates for 5 years, instead of the usual 9 months.
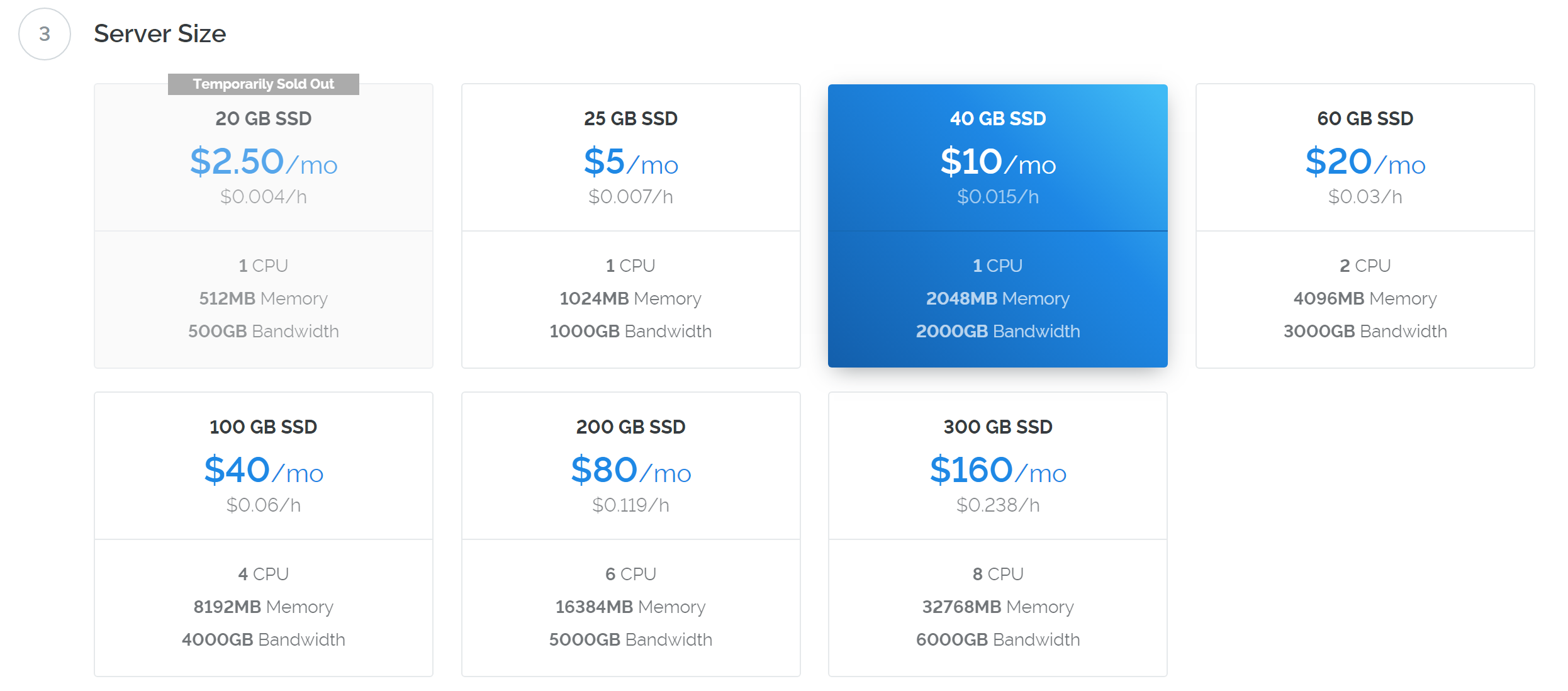
Selecciona un tamaño de servidor que ofrezca al menos 2 GB de memoria.
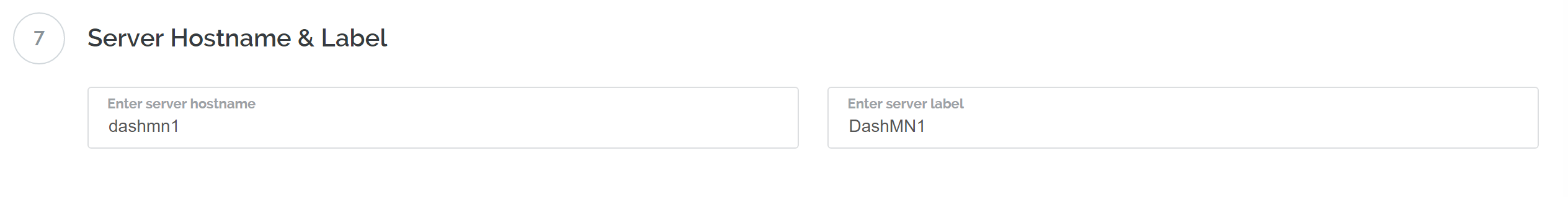
Ingresa un nombre de alojamiento y una etiqueta para tu servidor. En este ejemplo usaremos dashmn1 como nombre de alojamiento.
Vultr ahora instalará tu servidor. Este proceso puede tardar unos minutos.
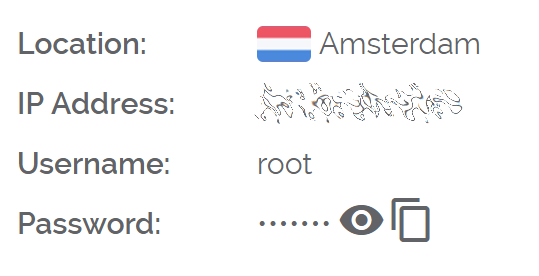
Haz click en Administrar cuando la instalación esté completa y toma nota de la dirección IP, el nombre de usuario y la contraseña.
Configurar tu sistema operativo¶
Comenzaremos por conectarnos a tu servidor recién provisto. En Windows, primero descargaremos una aplicación llamada PuTTY para conectarnos al servidor. Ve a la Página de descargas de PuTTY y selecciona el instalador MSI apropiado para tu sistema. En Mac o Linux puedes escribir ssh directamente desde el terminal - simplemente escribe ssh root@<server_ip> e ingresa tu contraseña cuando se le solicite.
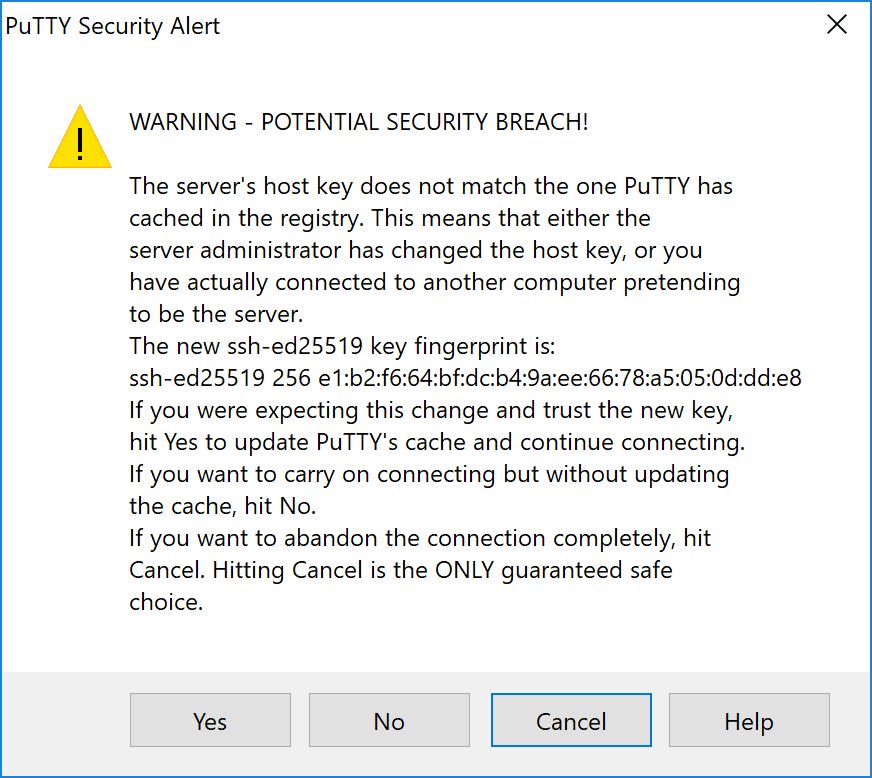
Haz doble click en el archivo descargado para instalar PuTTY, luego ejecuta la aplicación desde tu menú de Inicio. Ingresa la dirección IP del servidor en el campo Nombre de alojamiento y haz click en Abrir. Puedes ver una advertencia de certificado, ya que esta es la primera vez que te conectas a este servidor. Puedes hacer click con seguridad en Si para confiar en este servidor en el futuro.
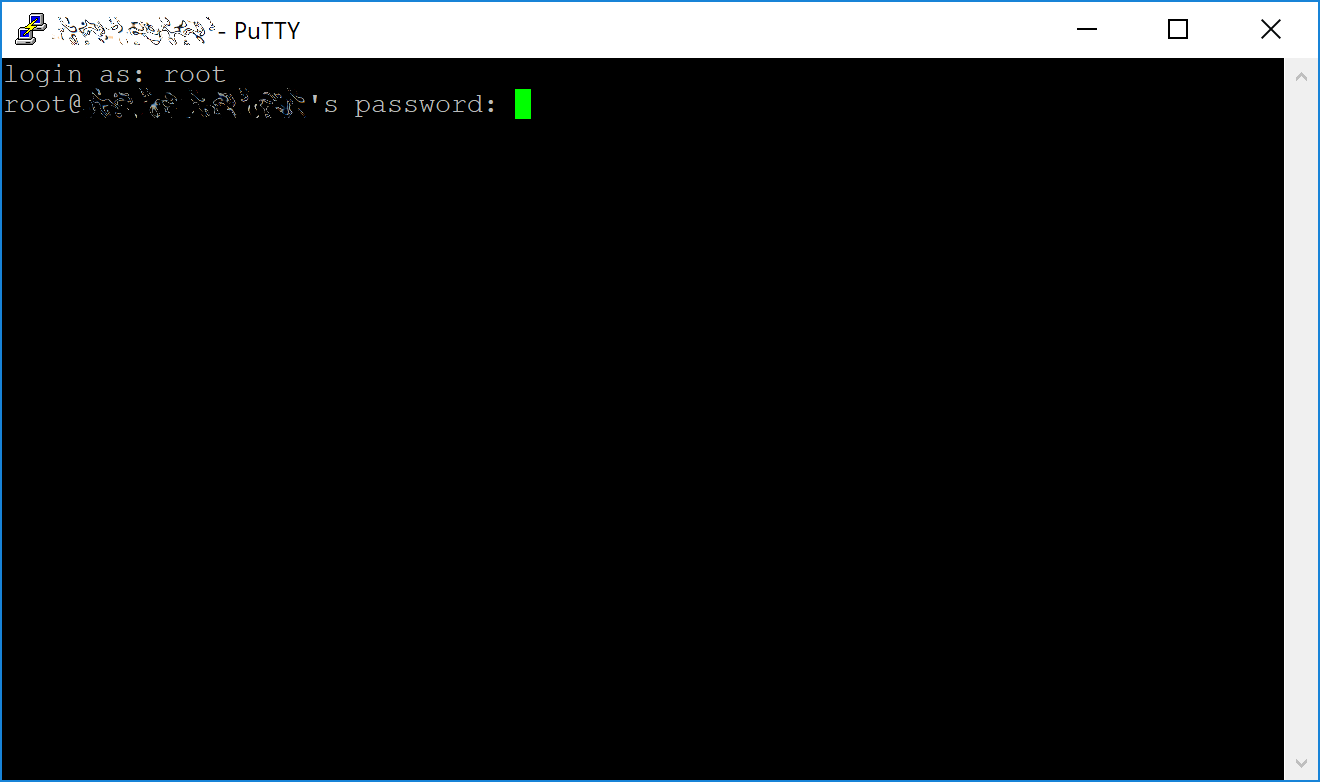
Ahora estás conectado a tu servidor y deberías ver una ventana de terminal. Comienza por iniciar sesión en tu servidor con el usuario root y la contraseña proporcionada por tu proveedor de alojamiento.
Deberías cambiar inmediatamente la contraseña de raíz y almacenarla en un lugar seguro para mayor seguridad. Puedes copiar y pegar cualquiera de los siguientes comandos seleccionándolos en tu navegador, presionando Ctrl + C, luego cambiando a la ventana PuTTY y haciendo click derecho en la ventana. El texto se pegará en la ubicación actual del cursor:
passwd root
Ingresa y confirma una nueva contraseña (preferiblemente larga y aleatoriamente generada). A continuación crearemos un nuevo usuario con el siguiente comando, reemplazando <username> con un nombre de usario de tu elección:
adduser <username>
Se te solicitará una contraseña. Ingresa y confirma usando una nueva contraseña (diferente a tu contraseña de raíz) y guárdala en un lugar seguro. También verás solicitudes de información del usuario, pero esto se puede dejar en blanco. Una vez que el usuario ha sido creado, lo agregaremos al grupo sudo para que puedan ejecutar comandos como raíz:
usermod -aG sudo <username>
Ahora, aunque todavía como raíz, actualizaremos el sistema desde el repositorio de paquetes de Ubuntu:
apt update
apt upgrade
El sistema mostrará una lista de paquetes actualizables. Presiona Y y Entrar para instalar los paquetes. Ahora instalaremos un firewall (y algunos otros paquetes que utilizaremos más adelante), agregaremos memoria de intercambio y reiniciaremos el servidor para aplicar las actualizaciones necesarias del kernel, y luego nos conectaremos a nuestro nuevo entorno seguro como el nuevo usuario:
apt install ufw python virtualenv git unzip pv
(presiona Y y Entrar para confirmar)
ufw allow ssh/tcp
ufw limit ssh/tcp
ufw allow 9999/tcp
ufw logging on
ufw enable
(presiona Y y Entrar para confirmar)
fallocate -l 4G /swapfile
chmod 600 /swapfile
mkswap /swapfile
swapon /swapfile
nano /etc/fstab
Agregua la siguiente línea al final del archivo (presiona la pestaña para separar cada palabra/número), luego presiona Ctrl + X para cerrar el editor, luego presiona Y y Entrar para guardar el archivo .
/swapfile none swap sw 0 0
Finalmente, en orden de prevenir ataques de hackeo de contraseñas por fuerza bruta, abra el archivo de configuración de SSH para deshabilitar el inicio de sesión de root en SSH:
nano /etc/ssh/sshd_config
Localiza la linea que dice PermitRootLogin yes y configura a PermitRootLogin no. Directamente debajo de esta, agregue una linea que diga AllowUsers <username>, remplazando <username> con el nombre de usuario que seleccionaste. Presione Ctrl + X para cerrar el editor, luego Y y Enter para guardar el archivo.
Luego reinicia el servidor:
reboot now
PuTTY se desconectará cuando el servidor se reinicie.
While this setup includes basic steps to protect your server against attacks, much more can be done. In particular, authenticating with a public key instead of a username/password combination, installing fail2ban to block login brute force attacks and enabling automatic security updates is advisable. More tips are available here. However, since the masternode does not actually store the keys to any Dash, these steps are considered beyond the scope of this guide.
Enviar garantía¶
A Dash address with a single unspent transaction output (UTXO) of exactly 1000 DASH is required to operate a masternode. Once it has been sent, various keys regarding the transaction must be extracted for later entry in a configuration file and registration transaction as proof to write the configuration to the blockchain so the masternode can be included in the deterministic list. A masternode can be started from a hardware wallet or the official Dash Core wallet, although a hardware wallet is highly recommended to enhance security and protect yourself against hacking. This guide will describe the steps for both hardware wallets and Dash Core.
Opción 1: enviar desde una billetera de hardware¶
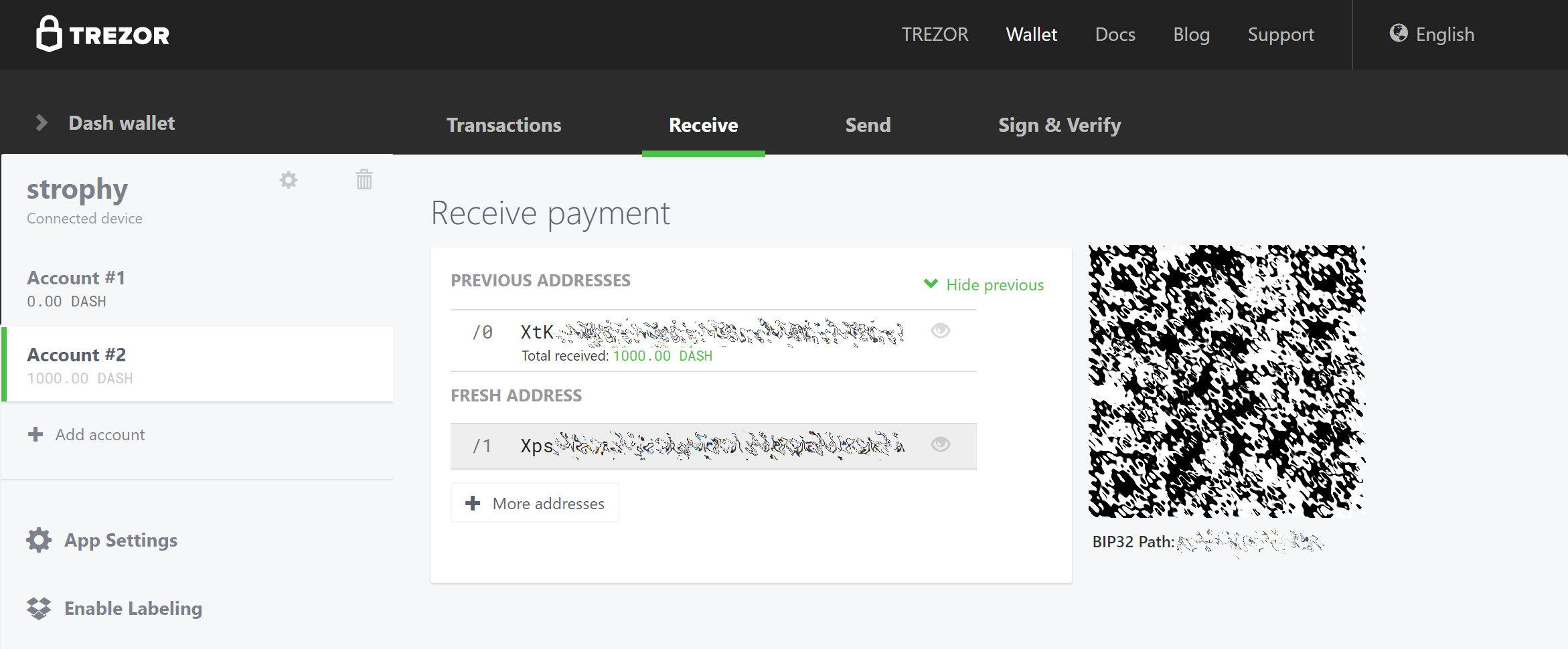
Set up your Trezor using the Trezor wallet at https://wallet.trezor.io/ and send a test transaction to verify that it is working properly. For help on this, see this guide - you may also choose to (carefully!) add a passphrase to your Trezor to further protect your collateral. Create a new account in your Trezor wallet by clicking Add account. Then click the Receive tab and send exactly 1000 DASH to the address displayed. If you are setting up multiple masternodes, send 1000 DASH to consecutive addresses within the same new account. You should see the transaction as soon as the first confirmation arrives, usually within a few minutes.
Una vez que aparece la transacción, haz click en el código QR a la derecha para ver la transacción en la cadena de bloques. Manten esta ventana abierta mientras completamos los siguientes pasos, ya que pronto necesitaremos confirmar que existen 15 confirmaciones, como se muestra en la siguiente captura de pantalla.
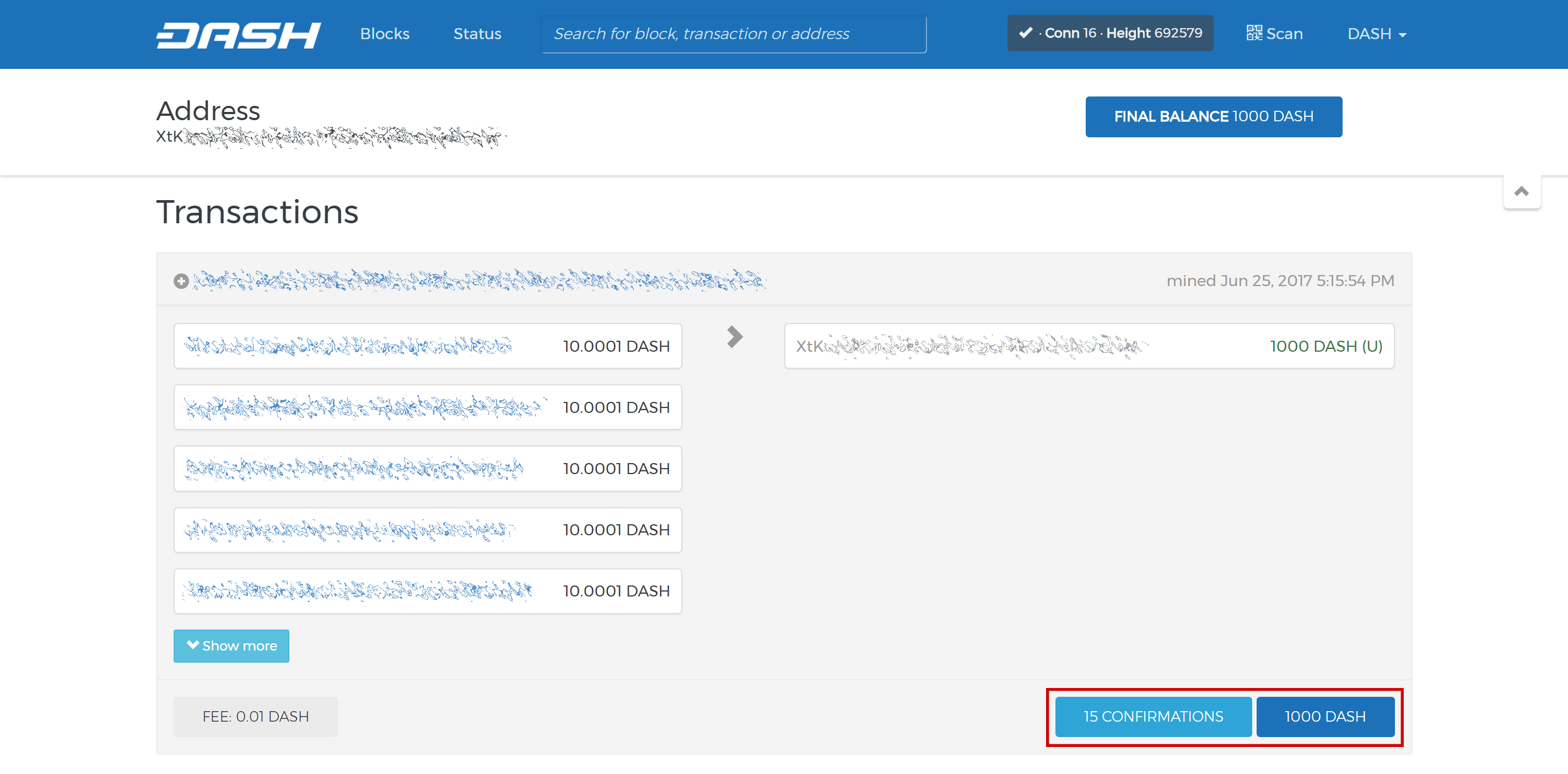
El explorador Trezor de la cadena de bloques muestra 15 confirmaciones para la transferencia de garantías
Mientras esperamos 15 confirmaciones, descarga la última versión de la herramienta Dash Masternode (DMT) desde la página de lanzamientos de GitHub aquí. Descomprime y ejecuta el archivo. La siguiente ventana aparecerá.
Click the third button from the left Check Dash Network Connection in the top left corner of the main window to verify that the connection is working. Then connect your Trezor device and click the next button Test Hardware Wallet Connection to verify the Trezor connection is working.
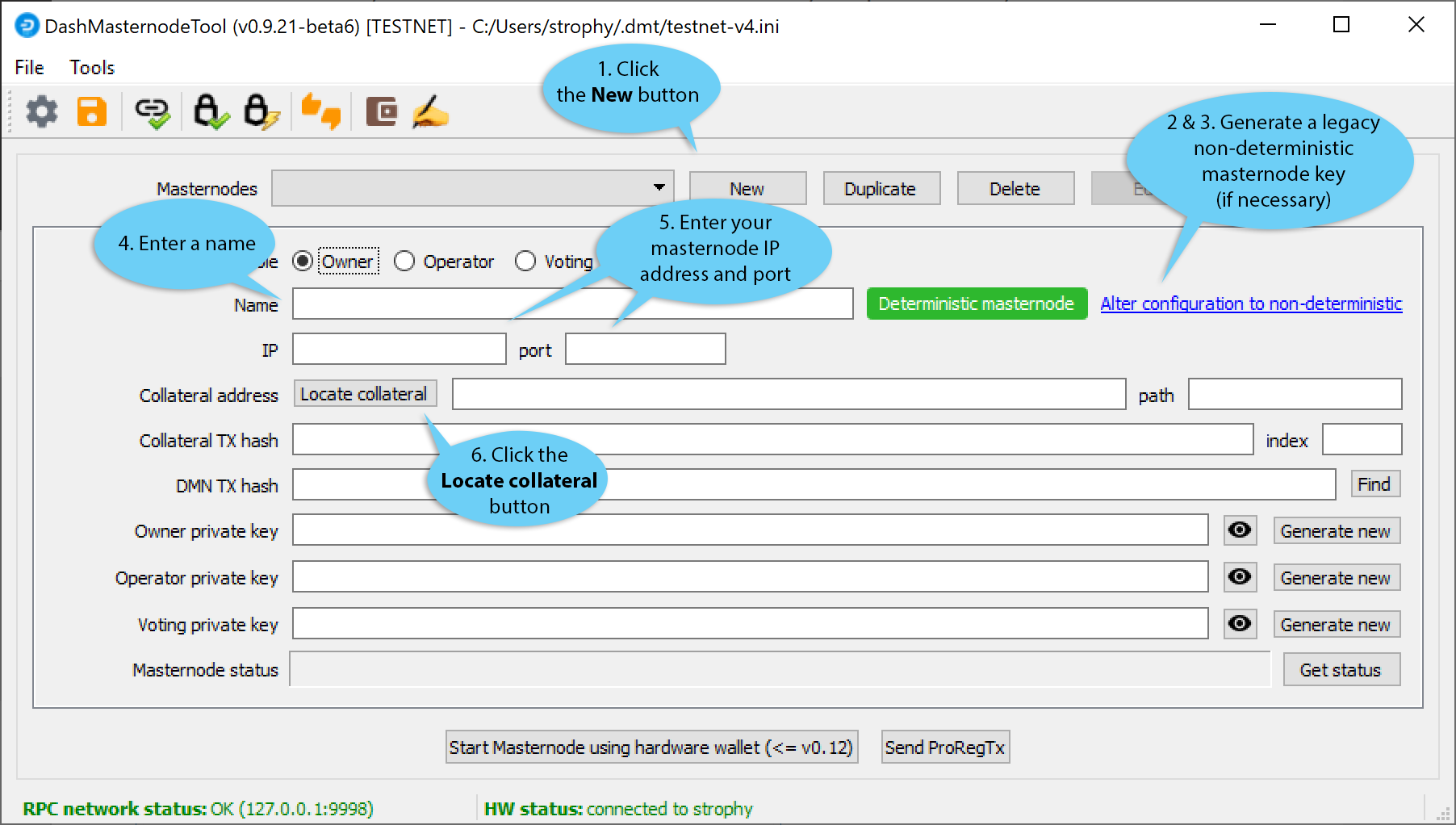
We will now use DMT to extract the transaction ID and legacy masternode key (necessary for successful startup during the DIP003 transition period). Carry out the following sequence of steps as shown in this screenshot:
- Click the New button.
- Ensure you are on the settings page for a Non-deterministic masternode and click Generate new to generate a legacy masternode key. Copy this key into a text editor.
- Click Alter configuration to deterministic
- Enter a name for your masternode. The host name you specified for your VPS above is a good choice.
- Enter the IP address of your masternode. This was given to you by the VPS provider when you set up the server.
- Ingresa el número del puerto TCP. Este debería ser 9999.
- Click Locate collateral to view unused collateral funding transactions available on the connected hardware wallet. The Collateral address, index and Collateral TX hash fields should be filled automatically
Leave DMT open and continue with the next step: installing Dash Core on your VPS.
Opción 2: enviar desde la billetera Dash Core¶
Abre la billetera Dash Core y espera a que se sincronice con la red. Debería verse así esto cuando esté lista:
Click Tools > Debug console to open the console. Type the following two commands into the console to generate a legacy masternode key (necessary for successful startup during the DIP003 transition period) and a new Dash address for the collateral:
masternode genkey
93PAqQsDjcVdYJHRfQPjsSt5338GCswMnUaSxoCD8J6fiLk4NHL
getnewaddress
yiFfzbwiN9oneftd7cEfr3kQLRwQ4kp7ue
Take note of the legacy masternode private key and collateral address, since we will need it later. The next step is to secure your wallet (if you have not already done so). First, encrypt the wallet by selecting Settings > Encrypt wallet. You should use a strong, new password that you have never used somewhere else. Take note of your password and store it somewhere safe or you will be permanently locked out of your wallet and lose access to your funds. Next, back up your wallet file by selecting File > Backup Wallet. Save the file to a secure location physically separate to your computer, since this will be the only way you can access our funds if anything happens to your computer. For more details on these steps, see here.
Now send exactly 1000 DASH in a single transaction to the new address you generated in the previous step. This may be sent from another wallet, or from funds already held in your current wallet. Once the transaction is complete, view the transaction in a blockchain explorer by searching for the address. You will need 15 confirmations before you can start the masternode, but you can continue with the next step at this point already: installing Dash Core on your VPS.
Instalar Dash Core¶
Dash Core es el software que está detrás de la billetera Dash Core GUI y Dash masternodes. Si no muestra una GUI, se ejecuta como un daemon en tu VPS (dashd), controlado por una interfaz de comando simple (dash-cli).
Abre PuTTY o una consola nuevamente y conéctate utilizando el nombre de usuario y la contraseña que acabas de crear para tu nuevo usuario que no sea raíz. Hay dos opciones para instalar Dash Core, una opción automatizada que utiliza una herramienta de guía llamada dashman por moocowmoo, miembro del equipo Dash Core, y una opción más complicada que te permitirá comprender todos los pasos de llave involucrados en la preparación de tu masternode.
Opción 1: instalación automatizada usando dashman¶
Para instalar Dash usando dashman, ingresa los siguientes comandos después de iniciar sesión:
cd ~
git clone https://github.com/moocowmoo/dashman
~/dashman/dashman install
(presiona Y y Entrar para confirmar)
dashman will download the latest version of Dash Core for your system, as well as an initial snapshot of the blockchain to speed up the bootstrapping process. Next download and install Sentinel, which is required for masternodes at version 0.12.1 or higher:
~/dashman/dashman install sentinel
Your system is now running as a standard Dash node, and is busy completing synchronisation with the blockchain. Since dashman does not automatically restart your masternode in the event of a system error, add a check function to crontab to make sure it checks every minute to ensure your masternode is still running:
crontab -e
Elije nano como tu editor e ingresa la siguiente linea al final del archivo, después de la linea para sentinel:
* * * * * pidof dashd || ~/.dashcore/dashd
Press enter to make sure there is a blank line at the end of the file, then press Ctrl + X to close the editor and Y and Enter save the file. Check the sync status and wait until all blockchain synchronisation and the 15 confirmations for the collateral transaction are complete:
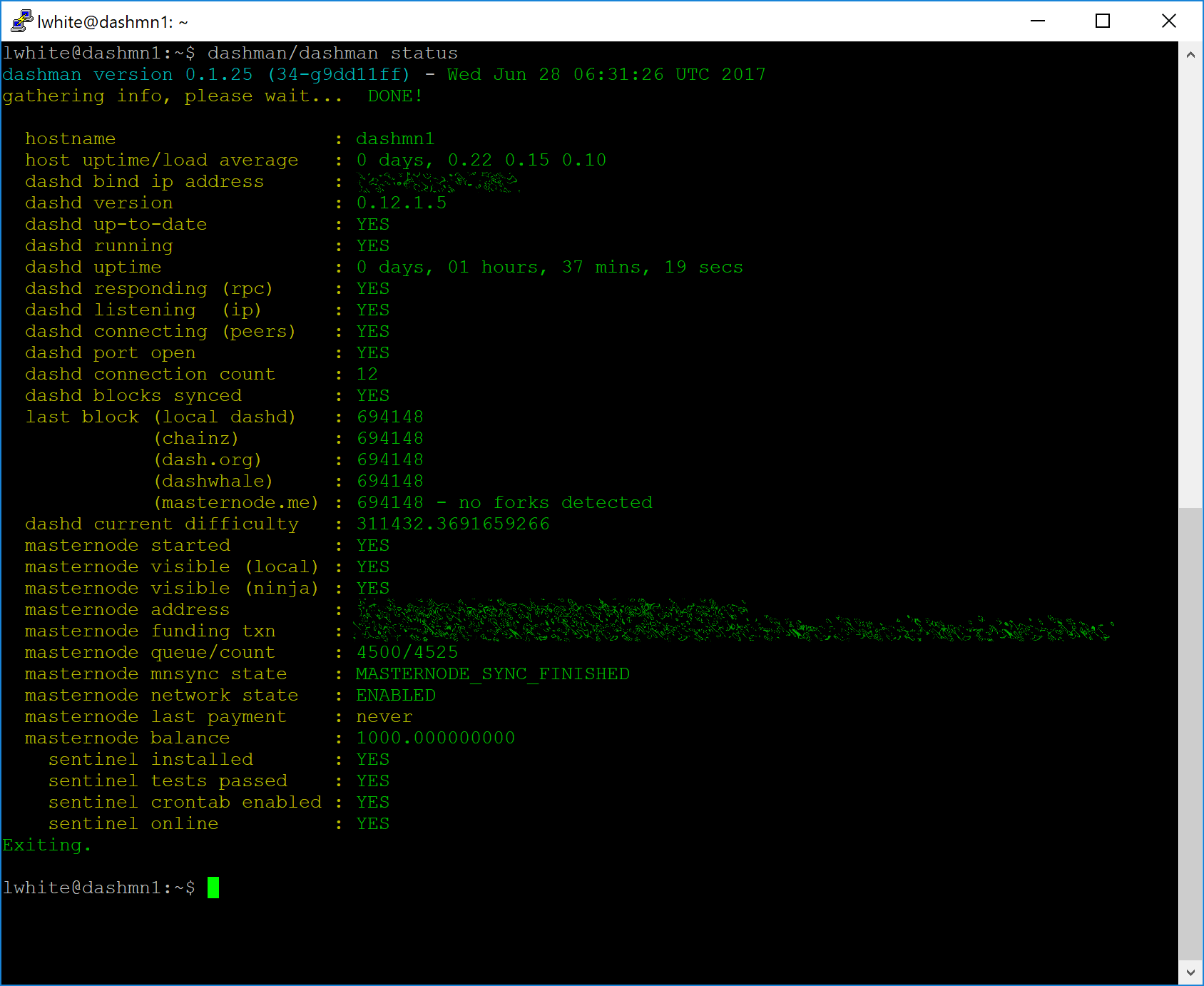
~/dashman/dashman status
Continue with the next step to register your masternode.
Opción 2: Manual de instalación¶
To manually download and install the components of your Dash masternode,
visit the GitHub releases page
and copy the link to the latest x86_64-linux-gnu version. Go back to
your terminal window and enter the following command, pasting in the
address to the latest version of Dash Core by right clicking or pressing
Ctrl + V:
cd /tmp
wget https://github.com/dashpay/dash/releases/download/v0.13.0.0-rc10/dashcore-0.13.0.0-rc10-x86_64-linux-gnu.tar.gz
Verify the integrity of your download by running the following command
and comparing the output against the value for the file as shown in the
SHA256SUMS.asc file:
wget https://github.com/dashpay/dash/releases/download/v0.13.0.0-rc10/SHA256SUMS.asc
sha256sum dashcore-0.13.0.0-rc10-x86_64-linux-gnu.tar.gz
cat SHA256SUMS.asc
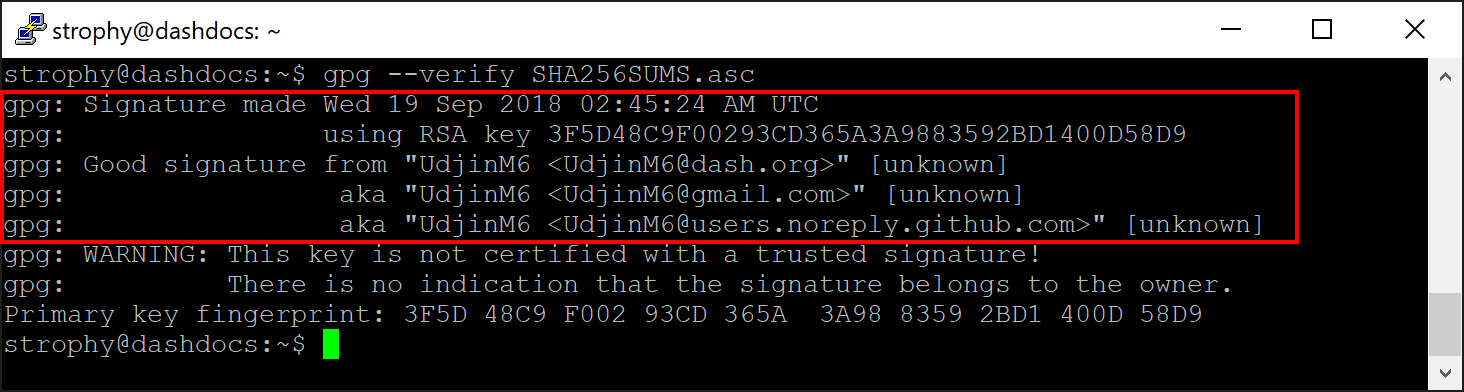
También puedes verificar opcionalmente la autenticidad de tu descarga como versión oficial del equipo Dash Core. Todos los lanzamientos de Dash están firmados usando GPG por UdjinM6 con la clave 8359 2BD1 400D 58D9, verificables aquí en Keybase. Importa la llave, descarga el archivo ASC para la versión actual de Dash y verifica la firma de la siguiente manera:
curl https://keybase.io/udjinm6/pgp_keys.asc | gpg --import
gpg --verify SHA256SUMS.asc
Create a working directory for Dash, extract the compressed archive and copy the necessary files to the directory:
mkdir ~/.dashcore
tar xfv dashcore-0.13.0.0-rc10-x86_64-linux-gnu.tar.gz
cp -f dashcore-0.13.0/bin/dashd ~/.dashcore/
cp -f dashcore-0.13.0/bin/dash-cli ~/.dashcore/
Crea un archivo de configuración usando el siguiente comando:
nano ~/.dashcore/dash.conf
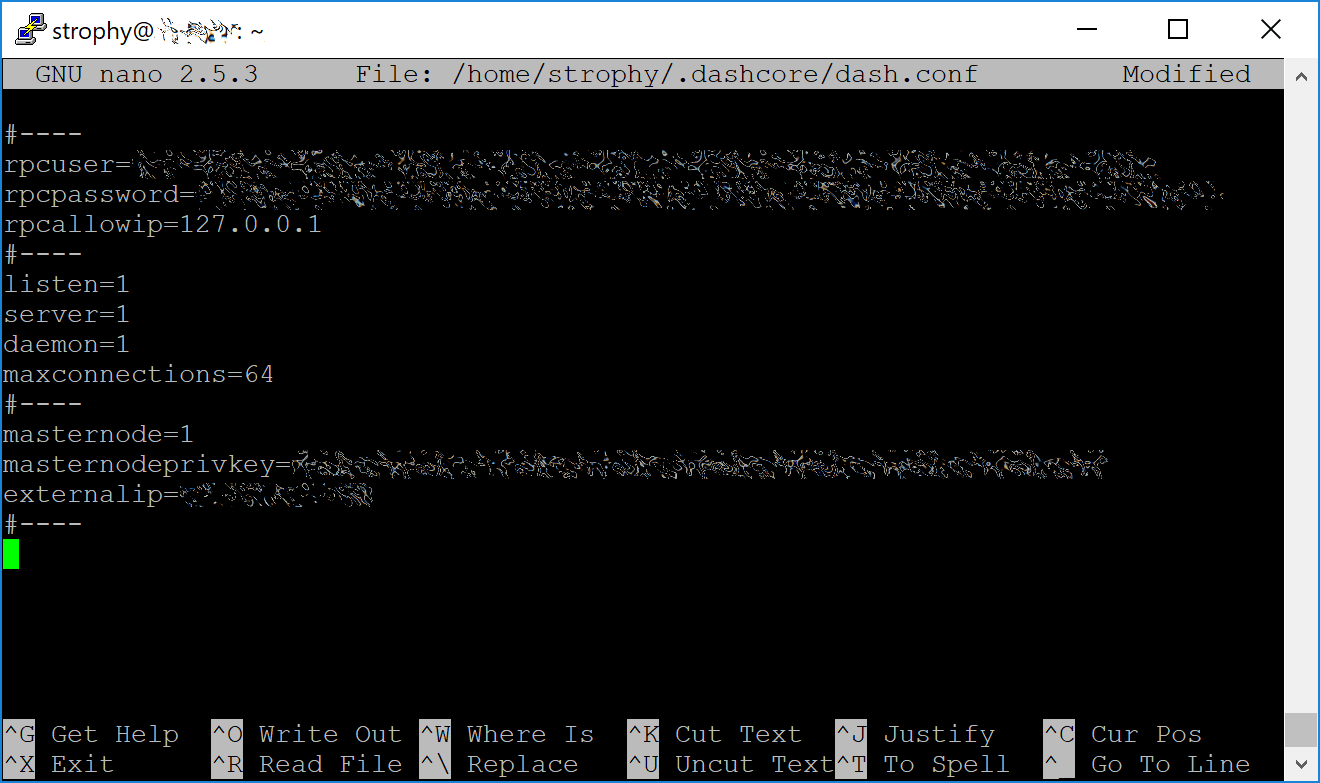
Aparecerá una ventana del editor. Ahora necesitamos crear un archivo de configuración que especifique varias variables. Copia y pega el siguiente texto para comenzar, luego reemplaza las variables específicas a tu configuración de la siguiente manera:
#----
rpcuser=XXXXXXXXXXXXX
rpcpassword=XXXXXXXXXXXXXXXXXXXXXXXXXXXX
rpcallowip=127.0.0.1
#----
listen=1
server=1
daemon=1
maxconnections=64
#----
masternode=1
masternodeprivkey=XXXXXXXXXXXXXXXXXXXXXXX
externalip=XXX.XXX.XXX.XXX
#----
Reemplaza los campos marcados con XXXXXXX de la siguiente manera:
rpcuser: ingresa cualquier cadena de números o letras, no se permiten caracteres especialesrpcpassword: ingresa cualquier cadena de números o letras, no se permiten caracteres especialesmasternodeprivkey: this is the legacy masternode private key you generated in the previous stepexternalip: esta es la dirección IP de tu VPS
El resultado debería verse más o menos así:
Presiona Ctrl + X para cerrar el editor y Y y Entrar para guardar el archivo. Ahora puedes comenzar a ejecutar Dash en el masternode para comenzar la sincronización con la cadena de bloques:
~/.dashcore/dashd
Verás un mensaje que dice Servidor de Dash Core comenzando. Ahora instalaremos Sentinel, un software que funciona como un perro guardián para comunicar a la red que tu nodo funciona correctamente:
cd ~/.dashcore
git clone https://github.com/dashpay/sentinel.git
cd sentinel
virtualenv venv
venv/bin/pip install -r requirements.txt
venv/bin/python bin/sentinel.py
Veras un mensaje que dice dashd no esta sincronizada con la red! Espere que este completa la sincronización antes de ejecutar Sentinel. Agrega dashd y sentinel a crontab para asegurar que se ejecuten cada minuto para verificar su masternode:
crontab -e
Elije nano como tu editor e ingresa las siguientes lineas al final del archivo:
* * * * * cd ~/.dashcore/sentinel && ./venv/bin/python bin/sentinel.py 2>&1 >> sentinel-cron.log
* * * * * pidof dashd || ~/.dashcore/dashd
Presiona entrar para asegurarte de que haya una línea en blanco al final del archivo, luego presiona Ctrl + X para cerrar el editor y Y y Entrar para guardar el archivo. Ahora debemos esperar a que se completen 15 confirmaciones de la transacción de garantía, y esperar a que la cadena de bloques termine de sincronizarse en el masternode. Puedes usar los siguientes comandos para monitorear el progreso:
~/.dashcore/dash-cli mnsync status
Cuando se completa la sincronización, deberías ver la siguiente respuesta:
{
"AssetID": 999,
"AssetName": "MASTERNODE_SYNC_FINISHED",
"Attempt": 0,
"IsBlockchainSynced": true,
"IsMasternodeListSynced": true,
"IsWinnersListSynced": true,
"IsSynced": true,
"IsFailed": false
}
Continue with the next step to construct the ProTx transaction required to enable your masternode.
Register your masternode¶
DIP003 introduces several changes to how a masternode is set up and operated. These are described briefly under DIP003 Masternode Changes in this documentation, or in full detail in DIP003 itself. It is highly recommended to first read at least the brief documentation before continuing in order to familiarize yourself with the new concepts in DIP003.
Option 1: Registering from a hardware wallet¶
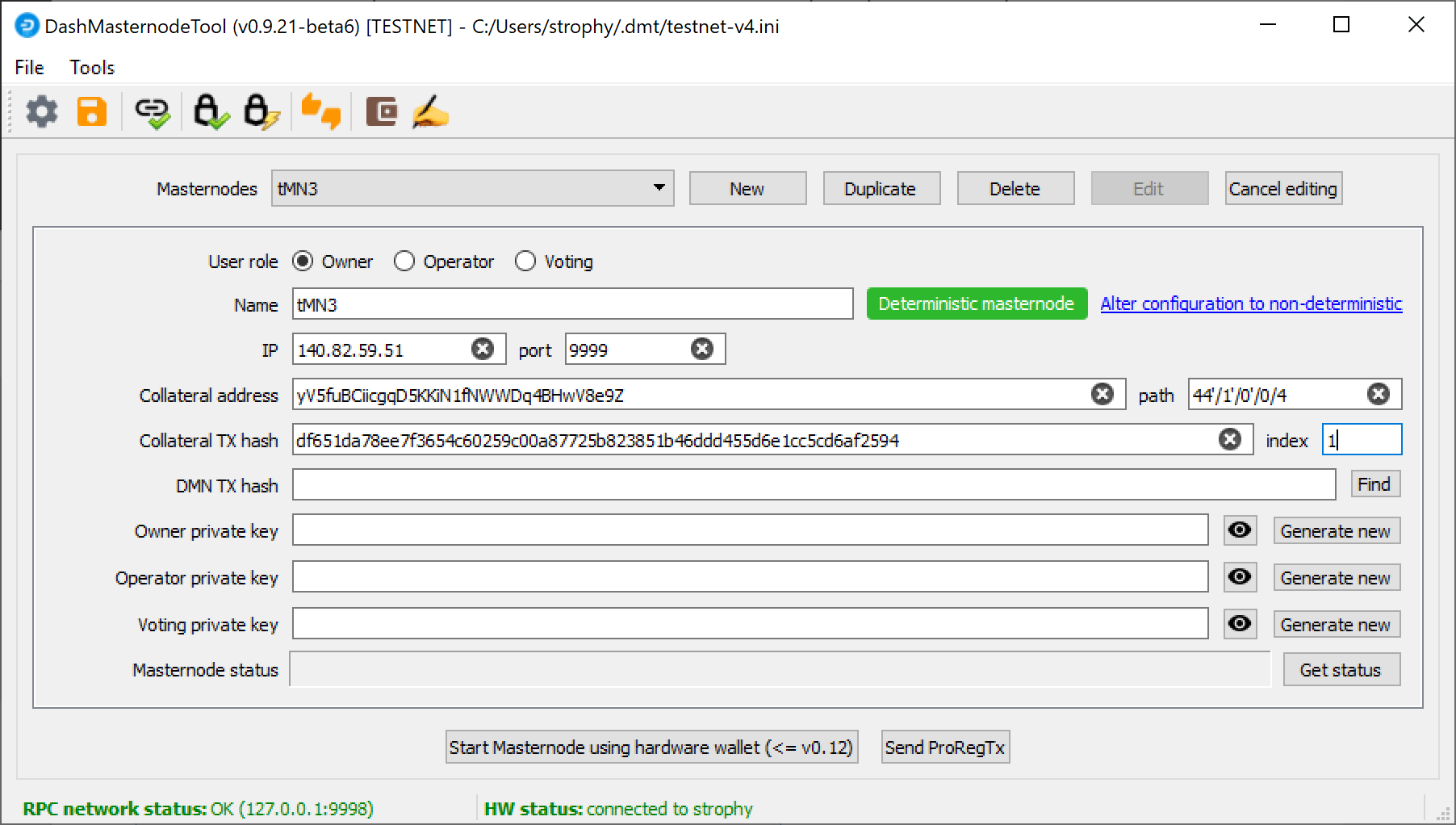
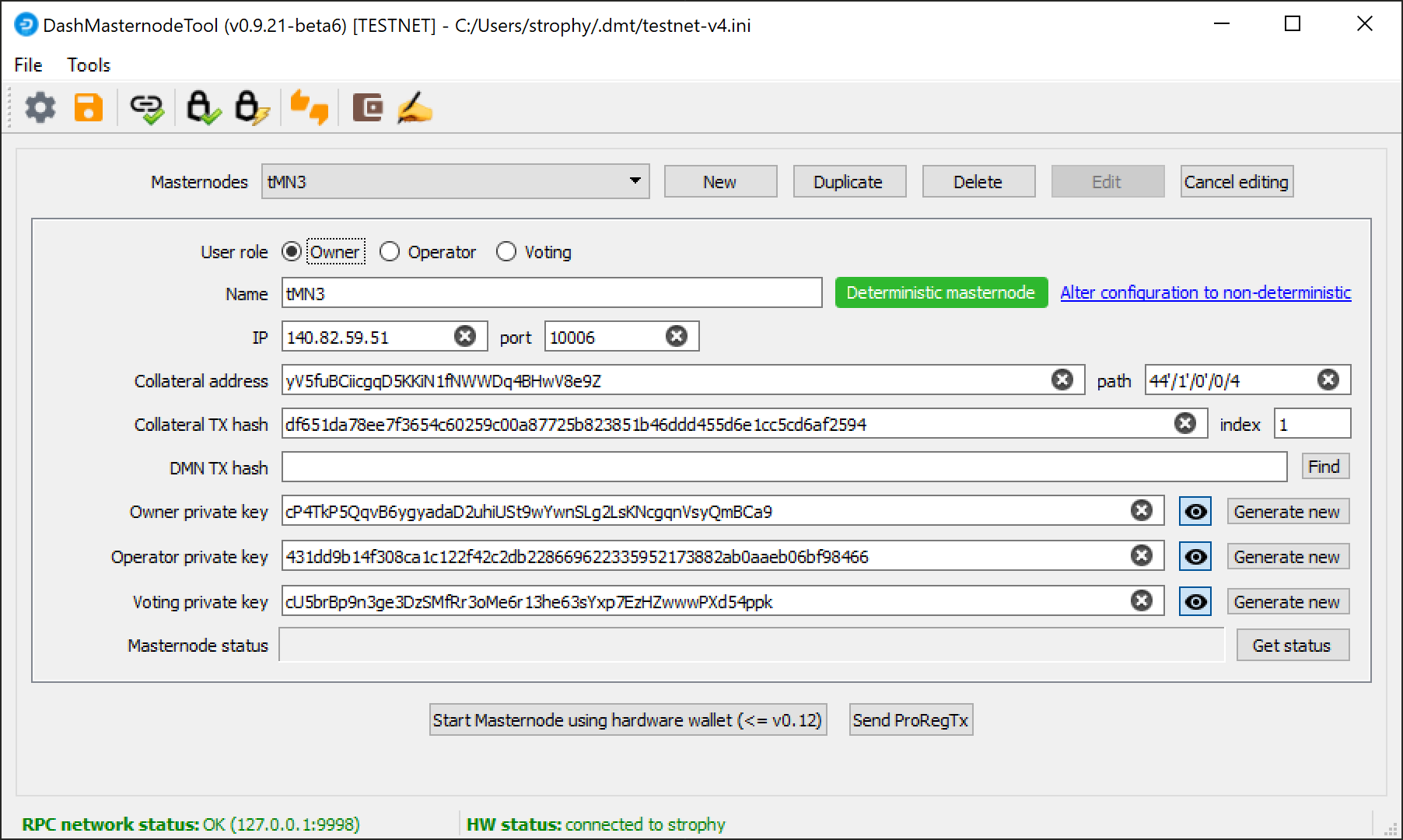
Go back to DMT and ensure that all fields from the previous step are still filled out correctly. Click Generate new for the three private keys required for a DIP003 deterministic masternode:
- Owner private key
- Operator private key
- Voting private key
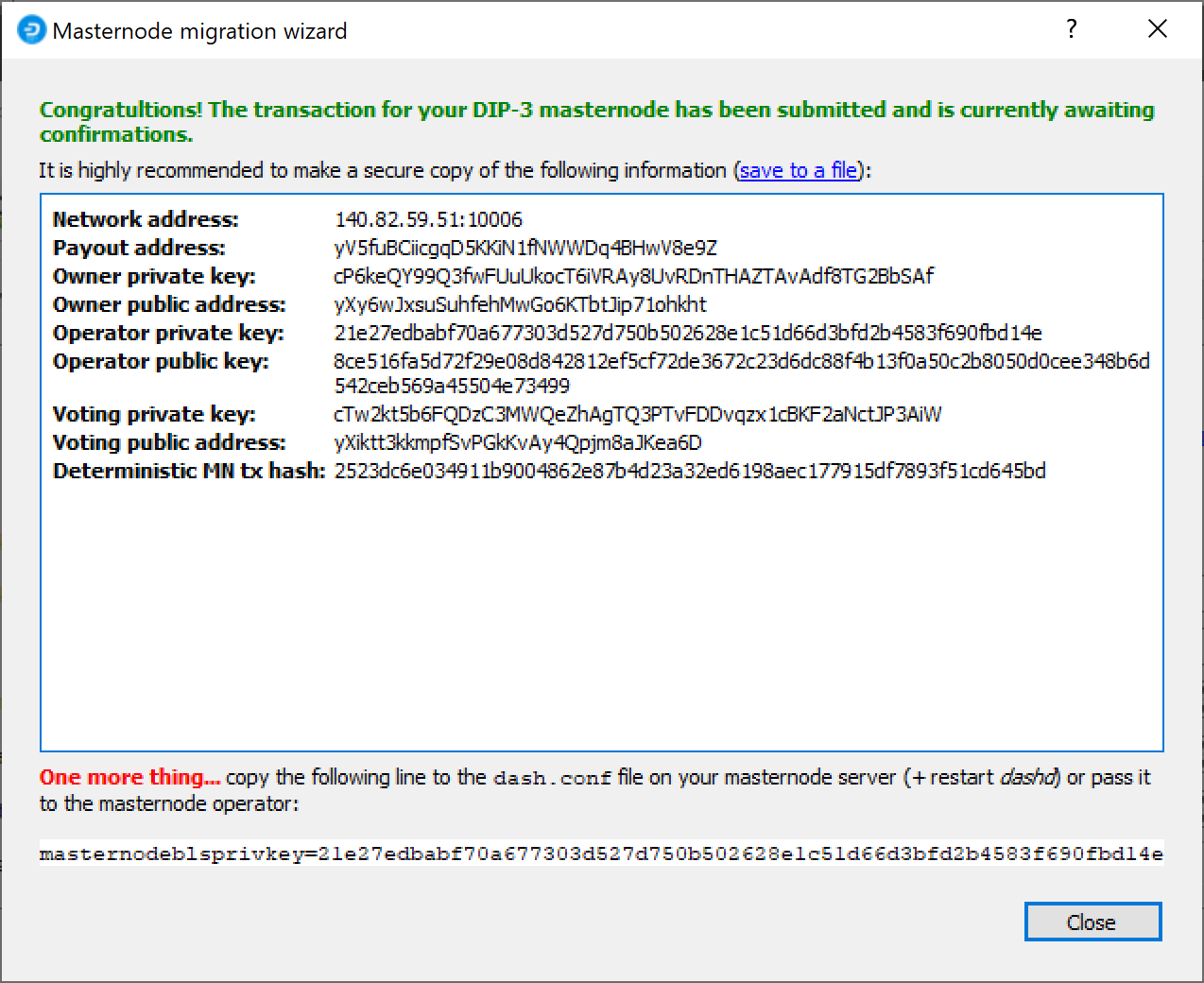
Then click Send ProRegTx and confirm the following two messages:
The BLS secret key must be entered in the dash.conf file on the
masternode. This allows the masternode to watch the blockchain for
relevant Pro*Tx transactions, and will cause it to start serving as a
masternode when the signed ProRegTx is broadcast by the owner, as we
just did above. Edit the configuration file on your masternode as
follows:
nano ~/.dashcore/dash.conf
The editor appears with the existing masternode configuration. Add this line to the end of the file, replacing the key with your BLS secret key generated above:
masternodeblsprivkey=21e27edbabf70a677303d527d750b502628e1c51d66d3bfd2b4583f690fbd14e
Press enter to make sure there is a blank line at the end of the file, then press Ctrl + X to close the editor and Y and Enter save the file. We now need to restart the masternode for this change to take effect. Enter the following commands, waiting a few seconds in between to give Dash Core time to shut down:
~/.dashcore/dash-cli stop
~/.dashcore/dashd
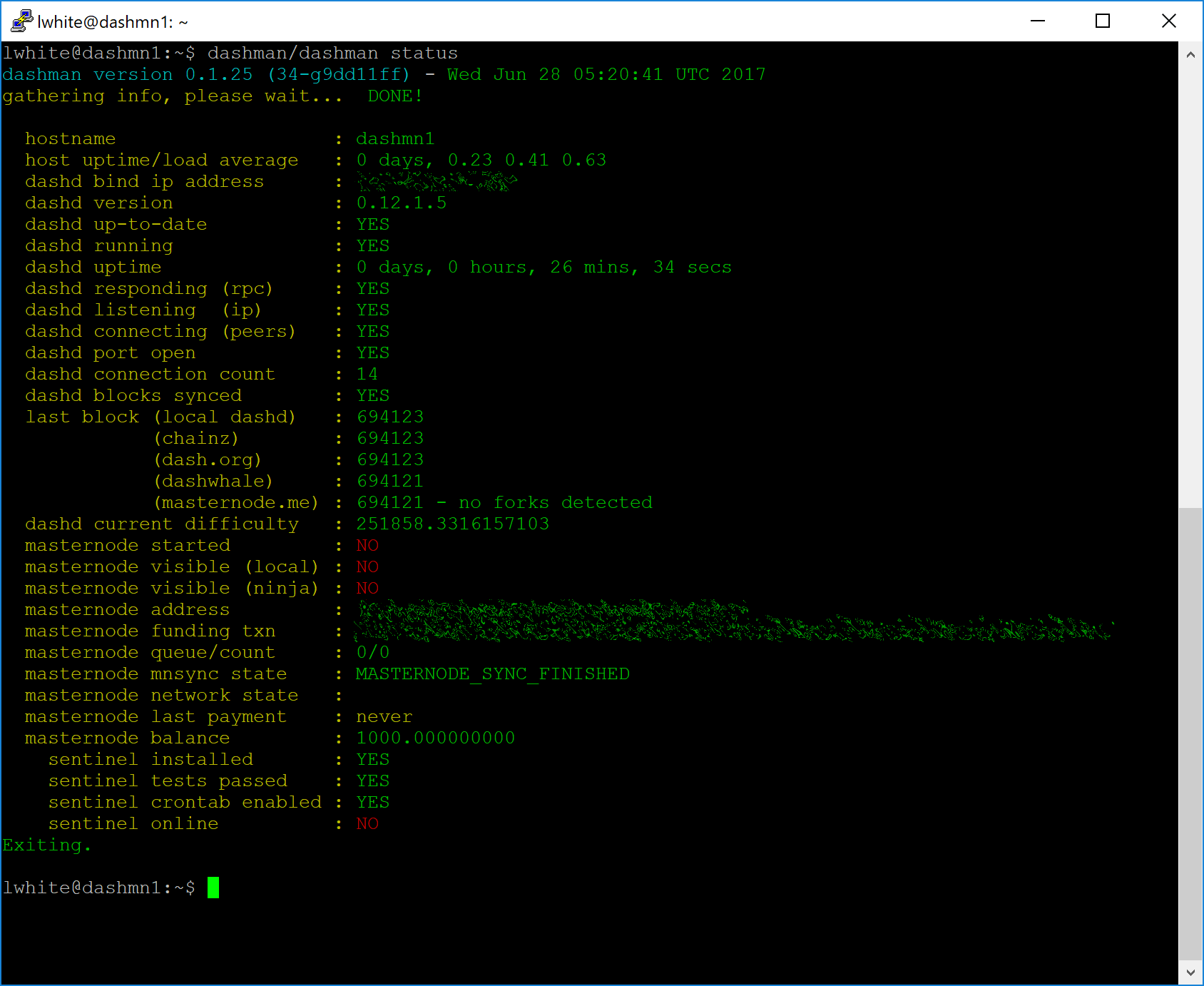
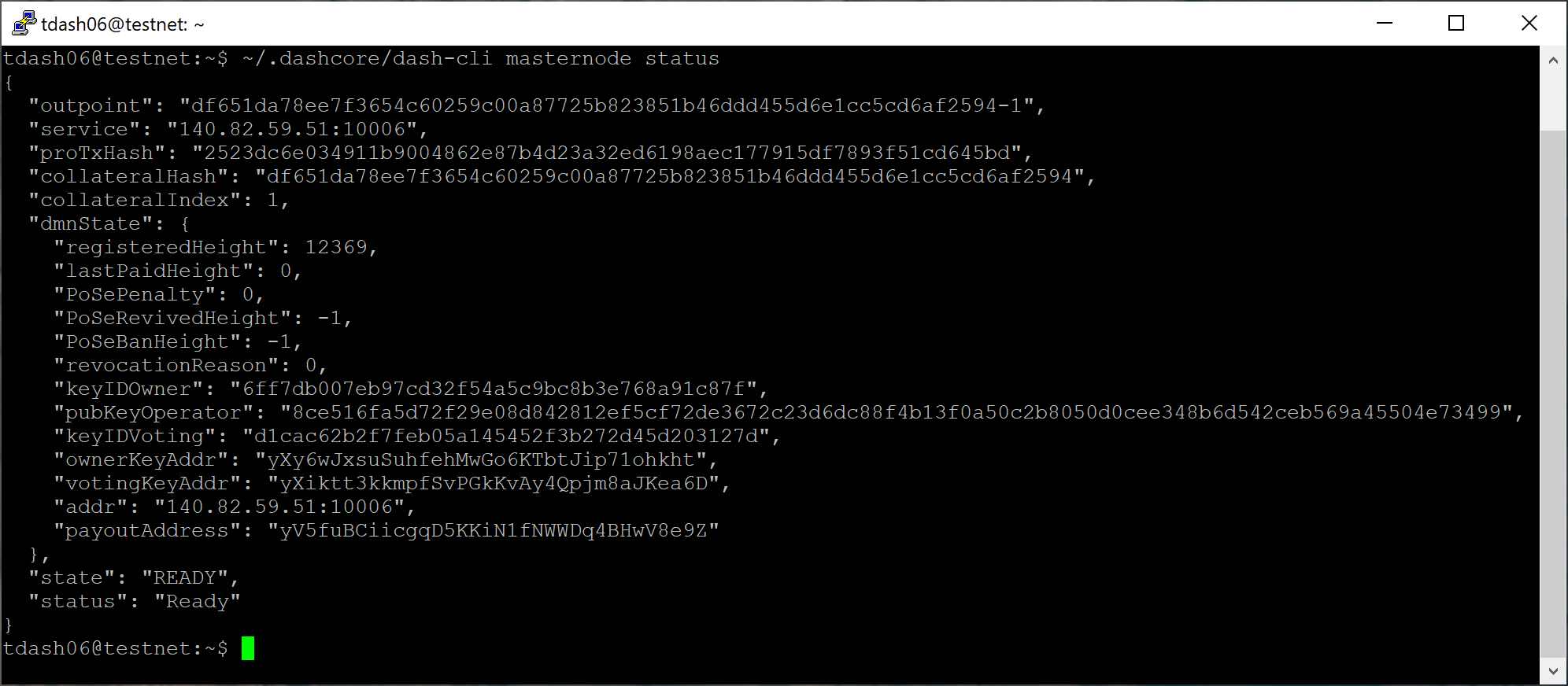
At this point you can monitor your masternode using
dashman/dashman status, by entering
~/.dashcore/dash-cli masternode status or using the Get status
function in DMT. The final result should appear as follows:
En este punto, puedes cerrar la sesión de tu servidor de manera segura escribiendo salir. ¡Felicitaciones! Tu masternode ahora se está ejecutando.
Option 2: Registering from Dash Core wallet¶
Identify the funding transaction¶
Si utilizaste una dirección en la billetera Dash Core para tu transacción de garantía, ahora necesitas encontrar el txid de la transacción. Haz click en Herramientas > Consola de depuración e ingresa el siguiente comando:
masternode outputs
Esto debería devolver una cadena de caracteres similar a esto:
{
"ad308ec104bdf113444be609eb3dce9474a5550424204c6538843e3ccd3d4e78" : "1",
}
The first long string is your transaction hash, while the last number is the index.
Generate a BLS key pair¶
A public/private BLS key pair is required for the operator of the masternode. If you are using a hosting service, they may provide you with their public key, and you can skip this step. If you are hosting your own masternode or have agreed to provide your host with the BLS private key, generate a BLS public/private keypair as follows:
bls generate
{
"secret": "28a85abb5aa8e820f65e33974cef0ab0bf06195f61454d2feb7fa578612d2228",
"public": "144cbf4d472716b9504a54c7ca26906a3346253b787ffeb1a4999325049f5b2c51ef2e7c215d85f0a9142ec1c78db99b"
}
These keys are NOT stored by the wallet and must be kept secure,
similar to the value provided in the past by the masternode genkey
command.
Add the private key to your masternode configuration¶
The public key will be used in following steps. The private key must be
entered in the dash.conf file on the masternode. This allows the
masternode to watch the network for relevant Pro*Tx transactions, and
will cause it to start serving as a masternode when the signed ProRegTx
is broadcast by the owner (final step below). Log in to your masternode
using ssh or PuTTY and edit the configuration file on your
masternode as follows:
nano ~/.dashcore/dash.conf
The editor appears with the existing masternode configuration. Add this line to the end of the file, replacing the key with your BLS secret key generated above:
masternodeblsprivkey=28a85abb5aa8e820f65e33974cef0ab0bf06195f61454d2feb7fa578612d2228
Press enter to make sure there is a blank line at the end of the file, then press Ctrl + X to close the editor and Y and Enter save the file. We now need to restart the masternode for this change to take effect. Enter the following commands, waiting a few seconds in between to give Dash Core time to shut down:
~/.dashcore/dash-cli stop
~/.dashcore/dashd
We will now prepare the transaction used to register a DIP003 masternode on the network.
Prepare a ProRegTx transaction¶
First, we need to get a new, unused address from the wallet to serve as the owner address. This is different to the collateral address. It must also be used as the voting address if Spork 15 is not yet active. Generate a new address as follows:
getnewaddress
yMwR1zf2Cv9gcMdHULRVbTTMGw7arvpbM5
Then either generate or choose an existing second address to receive the owner’s masternode payouts:
getnewaddress
yLqyR8PHEB7Fp1ue8nSuLfuxQhrj5PSTDv
You can also optionally generate and fund a third address to pay the
transaction fee. The private key to this address must be available to
the wallet submitting the transaction to the network. We will now
prepare an unsigned ProRegTx special transaction using the protx
register_prepare command. This command has the following syntax:
protx register_prepare collateralHash collateralIndex ipAndPort ownerKeyAddr
operatorPubKey votingKeyAddr operatorReward payoutAddress (feeSourceAddress)
Open a text editor such as notepad to prepare this command. Replace each argument to the command as follows:
collateralHash: The txid of the 1000 Dash collateral funding transactioncollateralIndex: The output index of the 1000 Dash funding transactionipAndPort: Masternode IP address and port, in the formatx.x.x.x:yyyyownerKeyAddr: The new Dash address generated above for the owner/voting addressoperatorPubKey: The BLS public key generated above (or provided by your hosting service)votingKeyAddr: The new Dash address generated above, or the address of a delegate, used for proposal votingoperatorReward: The percentage of the block reward allocated to the operator as paymentpayoutAddress: A new or existing Dash address to receive the owner’s masternode rewardsfeeSourceAddress: An (optional) address used to fund ProTx fee.payoutAddresswill be used if not specified.
Note that the operator is responsible for specifying their own
reward address in a separate update_service
transaction if you specify a non-zero operatorReward. The owner of
the masternode collateral does not specify the operator’s payout
address.
Example (remove line breaks if copying):
protx register_prepare
ad308ec104bdf113444be609eb3dce9474a5550424204c6538843e3ccd3d4e78
1
140.82.59.51:10004
yMwR1zf2Cv9gcMdHULRVbTTMGw7arvpbM5
144cbf4d472716b9504a54c7ca26906a3346253b787ffeb1a4999325049f5b2c51ef2e7c215d85f0a9142ec1c78db99b
yMwR1zf2Cv9gcMdHULRVbTTMGw7arvpbM5
0
yLqyR8PHEB7Fp1ue8nSuLfuxQhrj5PSTDv
Output:
{
"tx": "0300010001784e3dcd3c3e8438654c20240455a57494ce3deb09e64b4413f1bd04c18e30ad0000000000feffffff01cccfa204000000001976a9141ea44ced396667eb7d1c5b3699e04b5b3046ecfb88ac00000000d1010000000000784e3dcd3c3e8438654c20240455a57494ce3deb09e64b4413f1bd04c18e30ad0100000000000000000000000000ffff8c523b33271411c59262c9633a1bb810a7fc2b833c43cfa852ab144cbf4d472716b9504a54c7ca26906a3346253b787ffeb1a4999325049f5b2c51ef2e7c215d85f0a9142ec1c78db99b11c59262c9633a1bb810a7fc2b833c43cfa852ab00001976a91405c5fed6a3eb0b92ea5119039efae7a8dee5456488ac4e6cc5451440a6044dbd04d33a11f4cddc9021532ede3012ebbc31c0bb4ceb9c00",
"collateralAddress": "yiFfzbwiN9oneftd7cEfr3kQLRwQ4kp7ue",
"signMessage": "yLqyR8PHEB7Fp1ue8nSuLfuxQhrj5PSTDv|0|yMwR1zf2Cv9gcMdHULRVbTTMGw7arvpbM5|yMwR1zf2Cv9gcMdHULRVbTTMGw7arvpbM5|4e00de34ee03d28adb4e1fdaec966ae239c11da7e6115f566fc4b3f75c8a5503"
}
Next we will use the collateralAddress and signMessage fields to
sign the transaction, and the output of the tx field to submit the
transaction.
Sign the ProRegTx transaction¶
We will now sign the content of the signMessage field using the
private key for the collateral address as specified in
collateralAddress. Note that no internet connection is required for
this step, meaning that the wallet can remain disconnected from the
internet in cold storage to sign the message. In this example we will
again use Dash Core, but it is equally possible to use the signing
function of a hardware wallet. The command takes the following syntax:
signmessage address message
Example:
signmessage yiFfzbwiN9oneftd7cEfr3kQLRwQ4kp7ue yLqyR8PHEB7Fp1ue8nSuLfuxQhrj5PSTDv|0|yMwR1zf2Cv9gcMdHULRVbTTMGw7arvpbM5|yMwR1zf2Cv9gcMdHULRVbTTMGw7arvpbM5|4e00de34ee03d28adb4e1fdaec966ae239c11da7e6115f566fc4b3f75c8a5503
Output:
H3ub9BATtvuV+zDGdkUQNoUGpaYFr/O1FypmrSmH5WJ0KFRi8T10FSew0EJO/+Ij+OLv4r0rt+HS9pQFsZgc2dE=
Submit the signed message¶
We will now submit the ProRegTx special transaction to the blockchain to register the masternode. This command must be sent from a Dash Core wallet holding a balance, since a standard transaction fee is involved. The command takes the following syntax:
protx register_submit tx sig
Where:
tx: The serialized transaction previously returned in thetxoutput field from theprotx register_preparecommandsig: The message signed with the collateral key from thesignmessagecommand
Example:
protx register_submit 0300010001784e3dcd3c3e8438654c20240455a57494ce3deb09e64b4413f1bd04c18e30ad0000000000feffffff01cccfa204000000001976a9141ea44ced396667eb7d1c5b3699e04b5b3046ecfb88ac00000000d1010000000000784e3dcd3c3e8438654c20240455a57494ce3deb09e64b4413f1bd04c18e30ad0100000000000000000000000000ffff8c523b33271411c59262c9633a1bb810a7fc2b833c43cfa852ab144cbf4d472716b9504a54c7ca26906a3346253b787ffeb1a4999325049f5b2c51ef2e7c215d85f0a9142ec1c78db99b11c59262c9633a1bb810a7fc2b833c43cfa852ab00001976a91405c5fed6a3eb0b92ea5119039efae7a8dee5456488ac4e6cc5451440a6044dbd04d33a11f4cddc9021532ede3012ebbc31c0bb4ceb9c00 H3ub9BATtvuV+zDGdkUQNoUGpaYFr/O1FypmrSmH5WJ0KFRi8T10FSew0EJO/+Ij+OLv4r0rt+HS9pQFsZgc2dE=
Output:
b823338301e47875493c20361a23aef034578030c639480203b394669ab05e09
Your masternode is now registered and will appear on the Deterministic
Masternode List after the transaction is mined to a block. You can view
this list on the Masternodes -> DIP3 Masternodes tab of the Dash
Core wallet, or in the console using the command protx list valid,
where the txid of the final protx register_submit transaction
identifies your DIP003 masternode. Note again that all functions related
to DIP003 will only take effect once Spork 15 is enabled on the network.
You can view the spork status using the spork active command.
At this point you can go back to your terminal window and monitor your
masternode using dashman/dashman status, by entering
~/.dashcore/dash-cli masternode status or using the Get status
function in DMT. The final result should appear as follows:
En este punto, puedes cerrar la sesión de tu servidor de manera segura escribiendo salir. ¡Felicitaciones! Tu masternode ahora se está ejecutando.